Understand the Risks of Not Having a Secure Website
Over 80% of the top million websites either don't have a secure HTTPS website or they have one and aren't properly using it. This can cripple your business, even if you're not doing any financial transactions.
An HTTPS website creates a secure channel between you & your audience. Without it, anyone can intercept & change the conversation you're having. Imagine if you sent a letter to someone & the mail carrier opened it, read it, and then either modified it or inserted a different letter. That is the kind of thing that happens to websites that are not secured with HTTPS.
For the sake of abbreviate, there are two types of websites I want to talk about - HTTP and HTTPS. HTTPS websites often have a combination of green text in the browser's address bar and a padlock next to the website address. An HTTP site will have none of that.
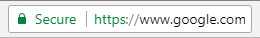 Secure HTTPS Website in the Chrome web browser.
Secure HTTPS Website in the Chrome web browser.
 Secure HTTPS Website in the Chrome web browser.
Secure HTTPS Website in the Chrome web browser.
Now maybe you're not a bank or a store that sells products on your website. It's common to think because you don't fall into one of these categories you don't need a secure website. Your website is still akin to the storefront of your company's brand or your personal brand. You are at least trying to sell your ideas to people. It's kind of like how I'm trying to sell you on securing your website. Needless to say you probably don't want to see someone taking your message & messing with it.
I keep mentioning someone messing with your website content and changing it. Without an HTTPS website, anyone can intercept your website's content & alter it before it gets to your visitors. Countries do it and Internet Service Provider's love to do it. From your local home internet provider, to hotels, gyms & even airplanes. You may not have even realized you experienced it. Many Internet Service Providers love to inject advertisements on to websites as a way to boost profits. My own internet provider tries to steal search results & get you to use their search engine.
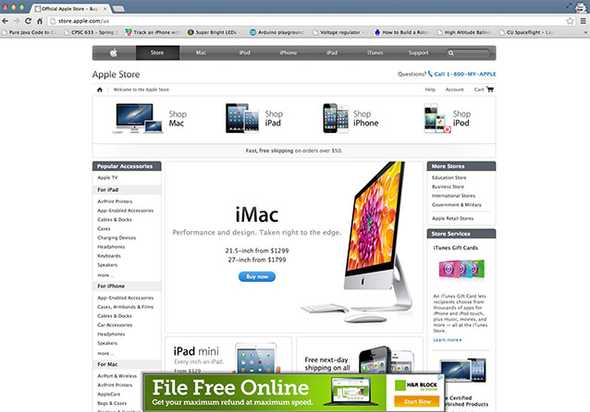 Apple's Store website at one time allowed you to browse the site before you ordered products with HTTP. Zachary Henkel captured this image of his Internet Service Provider CMA Communications injecting an H&R Block ad on to Apple's website.
Apple's Store website at one time allowed you to browse the site before you ordered products with HTTP. Zachary Henkel captured this image of his Internet Service Provider CMA Communications injecting an H&R Block ad on to Apple's website.
Let me stop you before you run away thinking "this isn't happening on my website, I just looked at it yesterday." Even though you don't see it when you visit your website, doesn't mean it's not happening to your customers. You may also be thinking that an H&R Block advertisement isn't going to stop people from buying the latest iMac. What if that H&R Block advertisement had been for a Windows Surface laptop instead?
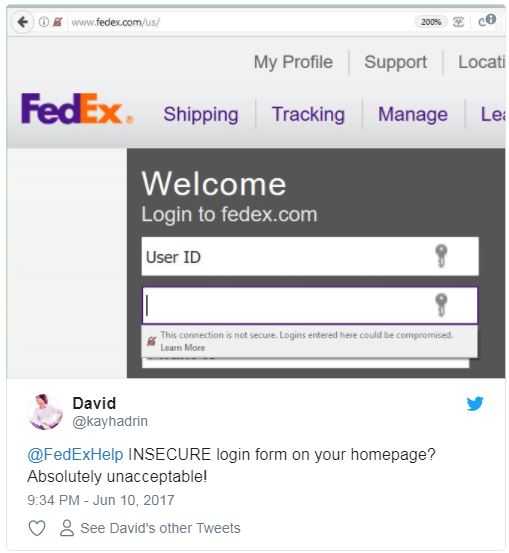
Insecure websites aren't only bad for your business, they're bad for your customers as well. If a customer fills out a form, someone at the same coffee shop or in the same airport could easily intercept the form. The website may never even receive the form submission. It's still common to see banks host login forms to the "secure" part of their website on a non-secure webpage. This has prompted companies like Google & Mozilla to start alerting users of Chrome & Firefox web browsers.
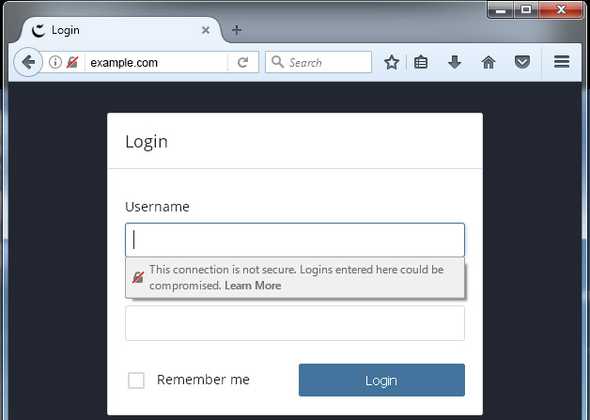 Firefox tries to warn users of insecure websites by showing a symbol next to the URL. Firefox also has a pop up as soon as you click on a username or password field on an insecure site
Firefox tries to warn users of insecure websites by showing a symbol next to the URL. Firefox also has a pop up as soon as you click on a username or password field on an insecure site
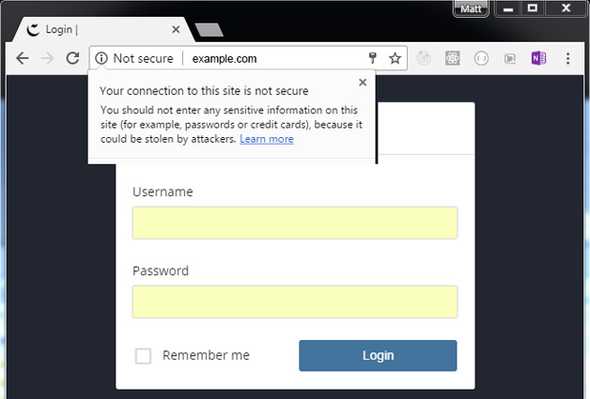 Chrome browsers label the website as not secure next to the address
Chrome browsers label the website as not secure next to the address
This becomes a huge problem for websites selling products and financial institutions. Customers will question doing business with websites that have any of the above warnings. There is also a high chance of getting called out on Twitter.
Creating a secure website is an easy process. You can get a free SSL Certificate at Let's Encrypt. Once you have it installed, you can test your implementation with services like SSL Labs. SSL Labs will give you suggestions on what to improve and how to do it. You can skip both these steps if you use a free service like CloudFlare. CloudFlare is a CDN that has an awesome free tier. You not only get a free SSL certificate but their implementation scores high marks on SSL Labs' tests.
Any HTTP Traffic is Bad Traffic
Enabling HTTPS is only half the battle. We also need to make sure to prevent any HTTP traffic at all.
Security researcher Troy Hunt did a demo showing what is possible if you simply try to redirect your visitors to the HTTPS website.
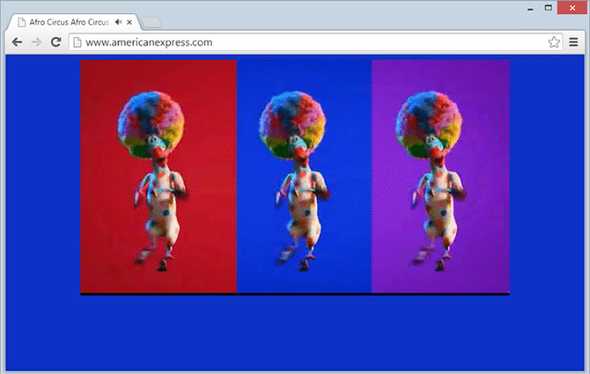 A demo of the American Express website's content redirected to a different website by Troy Hunt for anyone on the same network as him.
A demo of the American Express website's content redirected to a different website by Troy Hunt for anyone on the same network as him.
In the above image, Troy Hunt captures any HTTP requests to American Express and redirects them before the web server can. Troy did this by being on the same network as the computer trying to access American Express's website. In this demo, Troy makes the new website obvious. If Troy was doing this for malicious reasons though, he could have made a clone of American Express's website that sends all the visitor's data to him instead.
Once again there is an easy fix to this. It's an item in the SSL Labs test that is easy to overlook called HSTS & HSTS preloading. SSL Labs gives you a nice kudos if you implement this but it doesn't warn you if you don't. HSTS is a header (additional information) your website sends to the browser that says "only load this site using HTTPS, do not load this as a regular HTTP insecure website." HSTS tells the web browser to skip the HTTP request & send it directly to the HTTPS version of your website. HSTS prevents anyone from sneaking into your traffic conversation during the original HTTP request. If you use CloudFlare they offer a button to enable HSTS. Otherwise, you simply need to add the header to your website's responses.
One More Small Problem
Unfortunately HSTS has one problem. A user needs to visit your website at least once before your web browser learns of your HTTPS only requirement. That means on the first visit, someone who types in http://yourwebsite.com would still be sent to your HTTP version of your website before being redirected to the HTTPS version. We want to prevent that because it still provides a small opportunity for someone to intercept your website like Troy did. This is where the aforementioned HSTS preloading comes in. You can register your website at https://hstspreload.org/. By doing this, you are requesting the major web browsers to add you into a special list. That list tells their web browsers to never attempt an insecure HTTP request to your site.
There is one caveat to be aware of with HSTS Preload. When you add it on a domain, all sub-domains are included in the list automatically. That means if you register https://mywebsite.com, web browsers will expect sub-domains like https://dev.mywebsite.com to be HTTPS as well. For most websites, this is not a big deal. Especially since you can do it for free.
Additional Safety Benefits
If you have any form or if your site has sensitive data, you can run an extra set of tests at SecurityHeaders.io. Remember that statistic about less than 80% of the top million sites being secure? The majority of the ones that are secure, score low on this test. SecurityHeaders.io gives great guides on how to fix any test your site fails. Scoring a perfect score on this site can be a bit difficult though. Most of the tests are easy to pass for anyone with web server configuration experience.
Public-Key-Pins is one you may not want to implement. The risk of messing it up often outweighs the risk of someone using it to damage your website. Adding this incorrectly can wreck your website's domain name. At the same time, a recent exploit left all .io domains vulnerable to being hijacked. The only sites not vulnerable were sites that had HTTP Public Key Pinning and had been visited by the visitor's web browser at an earlier time.
Speed Benefits
Besides security, a faster website is one of the biggest impacts having a secure HTTPS website brings. Once you have a secure website you can use HTTP/2 which dramatically increases the speed of your website. Using HTTP/2 is like flying across the country instead of driving.
A common misconception is that secure websites are slower and cause more work on your web server due to encrypting traffic. Fortunately, they're not! It's a myth.
Besides speed you'll get several other perks when you implement HTTPS. Search engines like Google rank HTTPS sites higher. You will also have more reliable analytics on who visits your site.
If you're a business you need to make sure your entire site is secure using HTTPS only. Remember, HTTP traffic is bad traffic. HTTPS is free, easy & it protects both you & your customers. If you don't have an HTTPS certificate for your site, get one from Let's Encrypt. If Let's Encrypt looks complicated, try CloudFlare.
One Last Thing...
If you have a question or see a mistake, please comment below.
If you found this post helpful, please share it with others. It's the best thanks I can ask for & it gives me momentum to keep writing!